In this post we will see what the security parameters we should apply on our RHEL7 Linux machine in order to make it secure & prevent security related threats.
1) Create Strong Password: Brute-force is a technique which the hackers or intruder can use to break your system password.In order to secure your system you have to create any user with a strong (min 8 character long ) password.Use alphanumeric password with special character in order to make it strong. Redhat7 uses SHA512 has algorithm to make it encrypted so no one can read this password in /etc/passwd file. your hash passwords are stored in /etc/shadow file.There are several ways to create strong password mentioned below.
i)pwmake: This utility generates a strong random passwords for you.It consists
uppercase, lowercase, digits and special characters in order to generate passwords.You can use 56 to 128 bits to generate the strong password.
uppercase, lowercase, digits and special characters in order to generate passwords.You can use 56 to 128 bits to generate the strong password.
pwmake 128
ii)password strength checking: If you are a sys admin who work for an organization where you have to create multiple users then you might have to verify the password strength either its is strong enough or not.This can be done with the help of PAM module (pluggable authentication module) named pam_pwquality.so .This module checks the password strength against the set of rules. To enable the pam module, add the below line in /etc/pam.d/passwd:
password required pam_pwquality.so retry=3
password required pam_pwquality.so retry=3
You can configure the set of rules for your pam modules in
/etc/security/pwquality.conf
iii)Password Aging Configuration: You can set the password expiry date with the help of chage command. This will help you to make password secret after a certain period of use. See example below.
chage -M 90 username
Where -M is maximum number of days(90) after prompting for change the password for existing user (username).
Note: use -1 to disable the aging policy. use man pages for details.
iv)Account Lock Down: With this feature an account can be lockdown after the certain wrong attempts by user. This is done with the help of PAM module pam_faillock. All the fail login attempts will be saved in /var/run/faillock .
Follow the below steps in order to enable the account lock configuration.
step 1: Add the below two lines in auth section of the /etc/pam.d/system-auth and /etc/pam.d/password-auth files.
auth required pam_faillock.so preauth silent audit deny=3 unlock_time=600
auth [default=die] pam_faillock.so authfail audit deny=3 unlock_time=600
step 2: add the below line in account section of both files
account required pam_faillock.so
step3: To add rule for root user add even_deny_root option in auth section of the both files mentioned above.
2) Secure run level 1/single user mode:
In earlier system (RHEL6 RHEL5) you have to secure the run level 1 logins manually.you can set the password for runlevel 1/single user mode by editing the /etc/inittab file & add the below line.
For RHEL5
respawn:/sbin/sulogin
save the file & reboot the system or run /sbin/init q command to re-read the inittab file.
For RHEL6
"su:S:wait:/sbin/sulogin" before 'initdefault' line and edit the /etc/sysconfig/init and replace "SINGLE=/sbin/sushell" with "SINGLE=/sbin/sulogin"
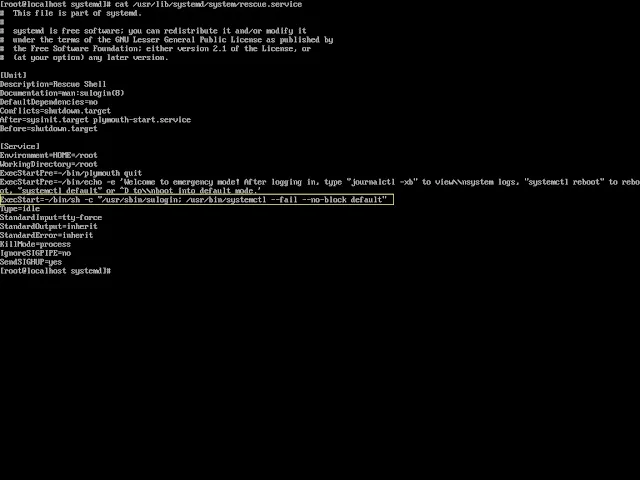
But this security is by defaults implemented in redhat7 Linux. This will prevent the access of our system when we boot machine to run level 1 / single user mode.In RHEL7 this service is now under the systemd daemon.By default, Single User mode is password protected by the root password on RHEL 7:
cat /usr/lib/systemd/system/rescue.service
cat /usr/lib/systemd/system/rescue.service
3)Secure GRUB Bootloader:
But the run level 1/single user mode can be bypass the root password by passing the “init=/bin/bash” command instead of 1 as the kernel parameter in GRUB .
So we have to protect our GRUB bootloader with a password.In order to protect our GRUB we have to follow below steps.
- open terminal with root access
- enter the command grub2-setpassword
- set password
- enter the command grub2-setpassword
- set password
You can see the password in /boot/grub2/user.cfg file which is encrypted with SHA512
By default this password for root user so keep in mind if asks for user enter as root
4)Secure OS from booting:
What if some how someone able to access the bootloader password / bypass it. You can further protect the machine by lockdown the OS from booting.
For this you have to go to /boot/grub2/grub2.cfg file.
- open the /boot/grub2/grub2.cfg file in any text editor.
- search for "--unrestricted" parameter in RHEL7 "menuentery" , and delete it.
- save & exit
- search for "--unrestricted" parameter in RHEL7 "menuentery" , and delete it.
- save & exit
Now your system will prompt for password when you boot it up.
Please note that changes to GRUB2 (/boot/grub2/grub.cfg) will be lost if you re generate the file using grub2-mkconfig commmand.
But If you delete the --unrestricted parameters from the menuenter in /boot/grub2/grub.cfg file , even then its is persisted with newly installed kernels images.So you password protection will not be losted.
5)Disable Interactive Startup:Pressing the I key at the
beginning of the boot sequence allows you to start up your system
interactively. During an interactive startup, the system prompts you to
start up each service one by one. However, this may allow an attacker
who gains physical access to your system to disable the security-related
services and gain access to the system.
To prevent users from starting up the system interactively, as root, disable the PROMPT parameter in the /etc/sysconfig/init file
PROMPT=no
6)Restricted Root Access: You can read here to restrict the root access here
Sharing is Caring😀

















0 Comments