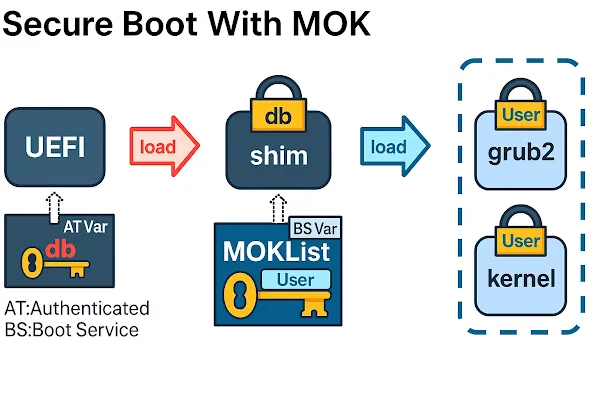
Machine Owner Key (MOK) is a user-generated cryptographic certificate that is used to extend the trust chain in a system that has UEFI Secure Boot enabled. It allows the system owner (you, the user or admin) to authorize and load third-party kernel modules, drivers, or custom kernels that are not signed by the OEM or Microsoft, while still keeping Secure Boot enabled and active.
📘 In Simple Terms:
MOKs are custom keys you create and register with your system to let it trust software (like drivers) that Secure Boot would otherwise block.
When Secure Boot is active, the firmware (BIOS/UEFI) will only boot software (bootloaders, kernels, drivers) that are signed by a trusted certificate. Out of the box, that usually means only Microsoft-signed or OEM-signed binaries.
This blocks third-party modules like:
- NVIDIA or AMD proprietary drivers
- VirtualBox kernel drivers
- VMware modules
- Custom-compiled kernels or kernel modules
By creating and enrolling a MOK, you can sign your own drivers or kernels, tell your system “Yes, I trust this,” and Secure Boot will allow it to load.
🛠️ How is a MOK Created?
You create a MOK with standard tools like OpenSSL:
openssl req -new -x509 -newkey rsa:2048 -keyout MOK.key -out MOK.crt -nodes -days 365You can then use this key to sign a module:
sign-file sha256 MOK.key MOK.crt module.koAnd enroll the certificate using:
sudo mokutil --import MOK.crtAfter reboot, you'll go through a screen called the MOK Manager, which lets you approve the key manually.
🧾 Where Are MOKs Stored?
MOKs are stored in the system's UEFI non-volatile memory (NVRAM). They're not part of your OS files, which makes them:
- Persistent across kernel updates
- Safe from file system changes
🛡️ Why Not Just Disable Secure Boot?
You can disable Secure Boot — but that turns off a major security layer meant to block boot-time malware (bootkits) and unauthorized kernel code.
- ✅ You keep Secure Boot enabled
- ✅ You stay secure
- ✅ You still load your custom drivers
🧩 MOK vs OEM Keys vs Microsoft Keys
| Key Type | Who Owns It? | Purpose |
|---|---|---|
| OEM Key (PK/KEK) | Your device vendor | Validates BIOS, bootloaders |
| Microsoft Keys | Microsoft | Loads Windows & signed Linux loaders |
| MOK | You (Machine Owner) | Lets you load trusted custom code |
📌 Summary
MOK = Machine Owner Key = User-trusted Secure Boot key.
- Allows you to load your custom drivers/modules even when Secure Boot is on.
- Managed via the mokutil tool and confirmed during reboot with the MOK Manager UI.
- Keeps your system flexible without sacrificing boot-level security.











0 Comments